General Information
The risk of targeted attacks and industrial espionage has become an increasing threat in today’s world. In recent years, malware has become much more common and sophisticated. The rate of virus alerts, data leaks and fraud has also considerably increased. As a result, the need for an experienced team consisting of skilled experts to handle these IT security threats has become urgent. Therefore, UITSEC established its own Cyber Security Incident Response Team in order to handle such security threats and support the leading organizations of in Turkey to solve urgent cyber security issues.
UITSEC Computer Security Incident Response Team (UITSEC CERT) provides a systematic response facility to handle computer security threats and incidents. It also provides the means for reporting incidents and distributing important incident-related information. In this way, your organization will be supported in terms of IT security threats and you will handle incidents just in time and in a more effective way.
UITSEC CERT serves to both public and private organizations. Our team provides a trusted point of contact for any organization for the handling of attacks and incidents. Its team of experts has the capability to react promptly and efficiently whenever threats are suspected, detected or incidents occur.
UITSEC CERT’s aim is to gather, review, report and respond to cyber threats in a systematic and prompt manner.
Mission Statement
UITSEC CERT’s aim is to protect the integrity of data, protect the speed and quality of access to information, prevent unauthorized access, protect privacy and confidentiality, ensure business continuity and performance in critical infrastructures.
“The necessary tools and information for performing attacks on cyberspace are often cheap and easily obtainable. The defense, however, is difficult and expensive. UITSEC CERT will provide a shield for you in this issue.”
UITSEC CERT’s main objectives are to determine the measures to be taken in relation to cyber security, provide the implementation of these measures within the framework of the prepared plans, programs and standards and manage the coordination of these.
UITSEC CERT’s missions are to:
- provide a systematic response facility to cyber security incidents,
- coordinate communication among national and international incident response teams during security emergencies and to help prevent future incidents,
- support both public and private organizations to recover quickly and efficiently from security incidents,
- minimize cyber security incident-based losses, theft of information and disruption of services,
- gather information regarding incident handling and security threats with an aim to better maintain future incident management as well as providing optimized protection for systems and data,
- provide an effective alert and warning system,
- continuously enhance the quality of cyber security solutions and raise awareness about the importance of cyber security for organization.
Constituency
UITSEC interacts with a wide range of organizations throughout Turkey. UITSEC CERT offers service to private and public organization which has a critical IT infrastructure to be protected. Logistics, energy, education and finance are the key sectors UITSEC CERT offers service to. On public side, our team mainly cooperates with municipalities. Furthermore, UITSEC CERT supports its constituents for establishing their own security operation center. When demanded, the team performs all operations and undertakes all processes for setting up a security operation center within the body of the constituent.
CERT Structure
UITSEC CERT structure is as follows:
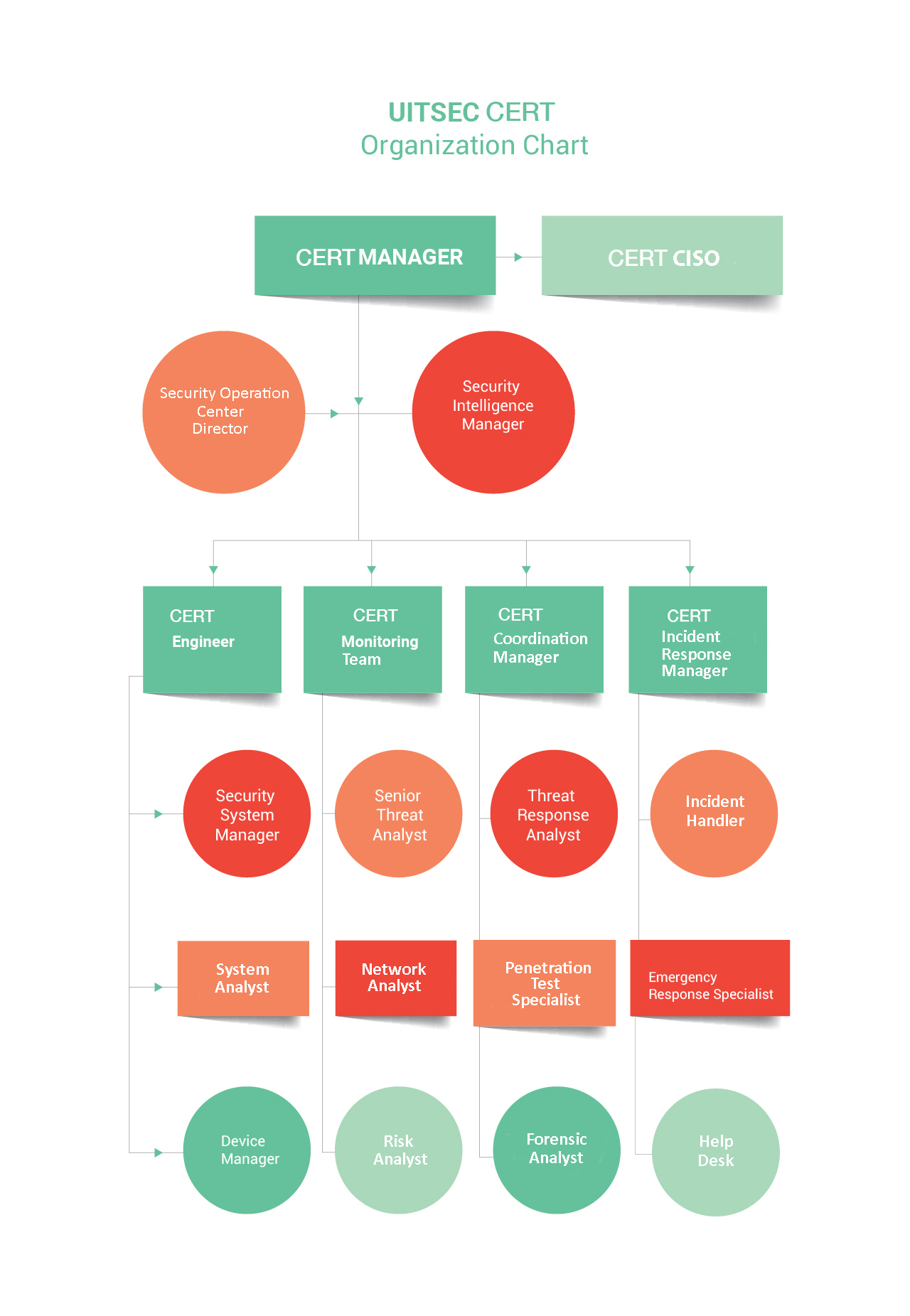
CERT Manager: CERT manager is responsible for the management of all security-related processes. CERT manager takes all security-related decisions. All tasks are assigned to the members of the team by the CSIRT manager.
CERT CISO: CERT CISO is responsible for the development and implementation of an effective information security program. CERT CISO proposes procedures and policies for the protection of systems, data and assets of the constituents.
SOC Director: SOC director is responsible for the management of all SOC operations. SOC director reviews all SOC policies and procedures. He leads the team and measures the performance of the staff.
Security Intelligence Manager: Security intelligence manager works in cooperation with SOC director. His main responsibility is to conduct threat analysis and inform the relevant team members when there is a suspicious activity. He takes action on alerts and incidents.
CERT Engineer: CERT engineer is responsible for monitoring, auditing and maintaining SOC systems. He reports security trends or problems to the management. He manages all security systems on organization’s network such as IDS and firewall.
CERT Monitoring Team: CERT monitoring team monitors all networks and analyzes traffic on those networks. The team monitors networks by using various tools for identifying potential threats or intrusions.
CERT Coordination Manager: CERT coordination manager enables the coordination to improve security posture and remediate security alerts as well as responding all security-related incidents.
CERT Incident Response Manager: CERT incident response manager manages the security incident response team in order to provide rapid response to emerging security threats. They analyze policies and procedures to be followed when responding an incident.
Security System Manager: Security system manager develops security measures for protecting systems against unauthorized access to critical information. System manager coordinates with the management and other teams in the organization.
Senior Threat Analyst: Senior threat analyst monitors all networks and detects suspicious activities. Threat analyst regularly reviews vulnerability assessment data by using the latest threat intelligence.
Threat Response Analyst: Threat response analyst explores the most effective tools or techniques to respond threats and incidents. He reviews and collects asset data for further investigation.
Incident Handler: Incident handler analyzes incident data, explores the potential impacts of an incident and acts properly to minimize the damage and recover services. He cooperates with all incident response team members.
System Analyst: System analyst examines all systems against potential threats or incidents. He analyzes system requirements and inform his manager in this regard. He also implements, configures and test applicable solutions.
Network Analyst: Network analyst manages all network-related issues on a daily basis. He plans, designs, analyzes and provides technical support for networks. He also conducts researches and evaluations for the purchase of the required network equipment.
Penetration Test Specialist: Penetration test specialist exploits the vulnerabilities and detect whether the system is vulnerable or not. He performs penetration tests on the most critical infrastructure components of its constituents.
Emergency Response Specialist: Emergency response specialist evaluates the existing policies and procedures to determine the areas to be improved within the scope of emergency response. He defines effective emergency response strategies. He trains emergency personnel to effectively respond incidents.
Device Manager: Device manager manages the security of all devices used in the organization. He regularly monitors, controls and reviews the security posture of all devices. He performs all configurations of devices and checks whether there are vulnerable points.
Risk Analyst: Risk analyst collects information about the potential risks against the data, assets and systems of the organization. He uses his knowledge to suggest risk improvement strategies.
Forensic Analyst: Forensic analyst preserves, identifies, extracts and documents evidence stored on systems. He searches the systems for collecting information that will be used to prove that a crime has been committed.
Help Desk: Help desk is responsible for submitting all the reported incidents to CSIRT through all means of communication. Help desk then forwards the reported incident to the incident handlers after proper categorization of the reported incident.


