In today’s world, there are three types of organizations.
- Organizations that have been breached
- Organizations that don’t yet know they have been breached
- Organizations that will be breached
The difference between these three types of organizations is about whether they can detect threats or breaches in a very short time and respond to them effectively or not. UITSEC CERT enables an effective functioning and management of organizations in terms of cyber security with its security professionals. UITSEC CERT offers the essential information to organizations in order that they can detect threats just in time. As well as detecting and solving problems, UITSEC CERT places special importance to incident response.
UITSEC CERT SERVICES
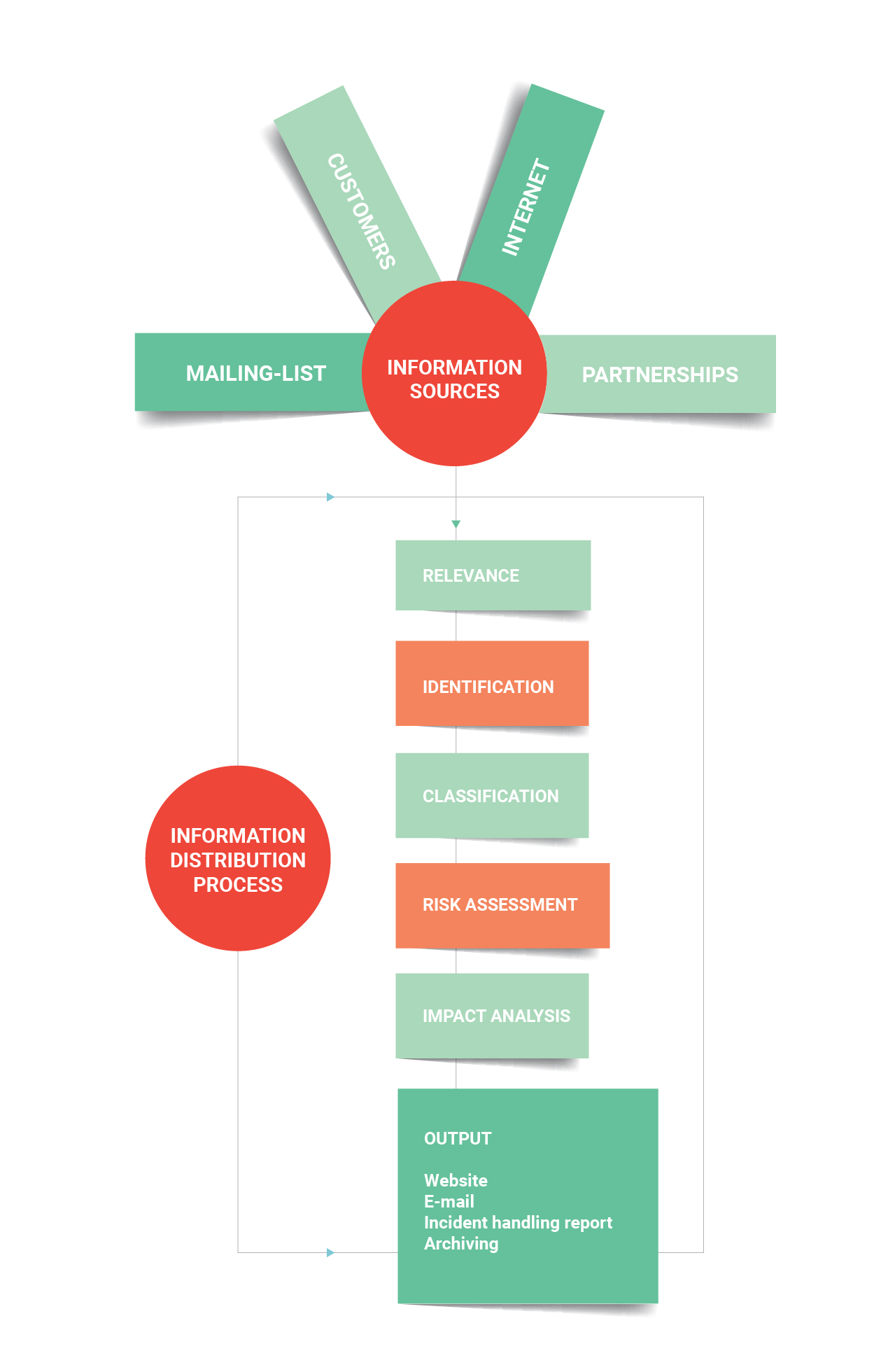
UITSEC CERT has professional experts within different fields of IT security including forensics, incident response, network and penetration test. Our team of experts is responsible for 24/7 monitoring and investigation of potential threats and response to emerging cyber security incidents. The members of UITSEC CERT work on the latest trends and methodologies. Apart from its specialist knowledge, the team focuses on keeping an eye on potential threats against your organization. UITSEC CERT also benefits from the Incident Response Kit (IRK) with an aim to collect digital evidence in a simple and effective way in order to handle IT security issues.
UITSEC CERT provides system support to specialists in the field of IT security with various tools such as monitoring modules that control your organization on the Internet and your internal network, forensic case handling system, toolbox and insight articles on the most recent threats.
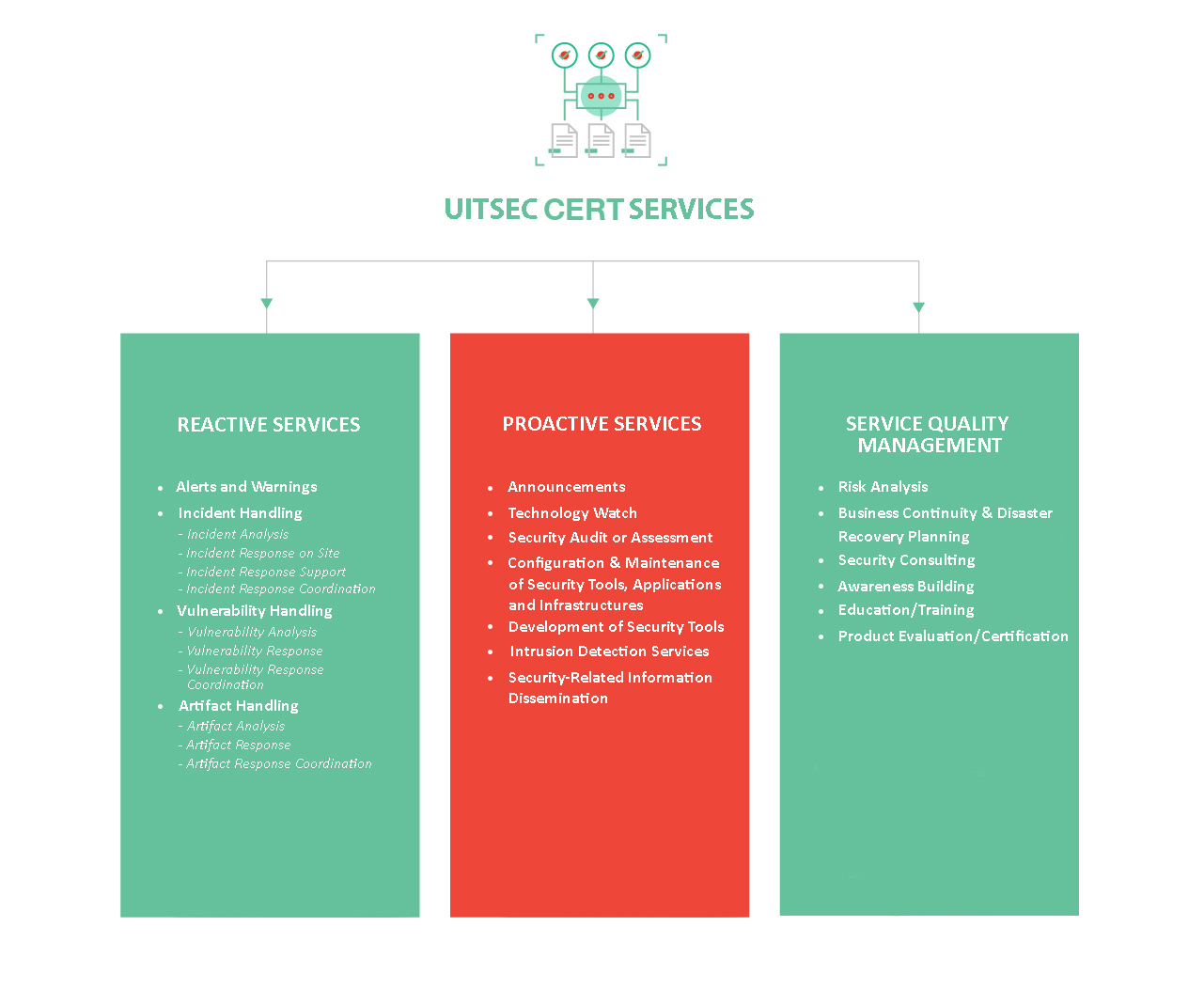
As also seen in the list above, UITSEC CERT offers three types of core services:
1) Reactive Services
2) Proactive Services
3) Security Quality Management Services
SERVICE DESCRIPTIONS
1) Reactive Services focus on responding demands or incident reports obtained from the constituents. In this service category, compromised hosts, malware, threats and vulnerabilities are responded in an effective way. Furthermore, protection, recovery, rebuilding and improvement of systems are targeted. Some of the services in this category are listed below:
- Alerts & Warnings: distribution of any information regarding attacks, threats, vulnerabilities, intrusions, viruses and system failures, notifying the constituents about the potential or emerging security issues, providing guidance for the protection or recovery of any affected systems.
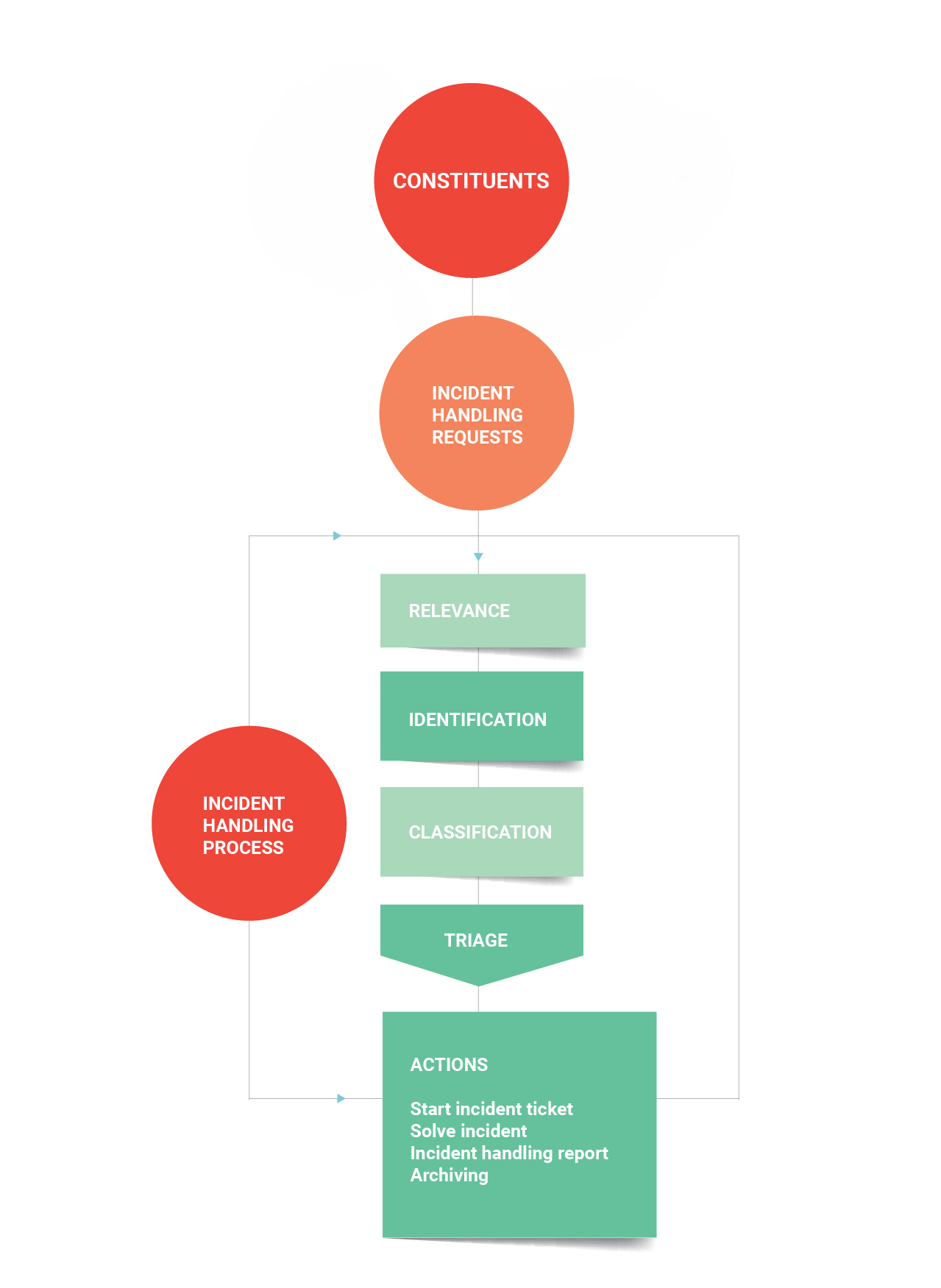
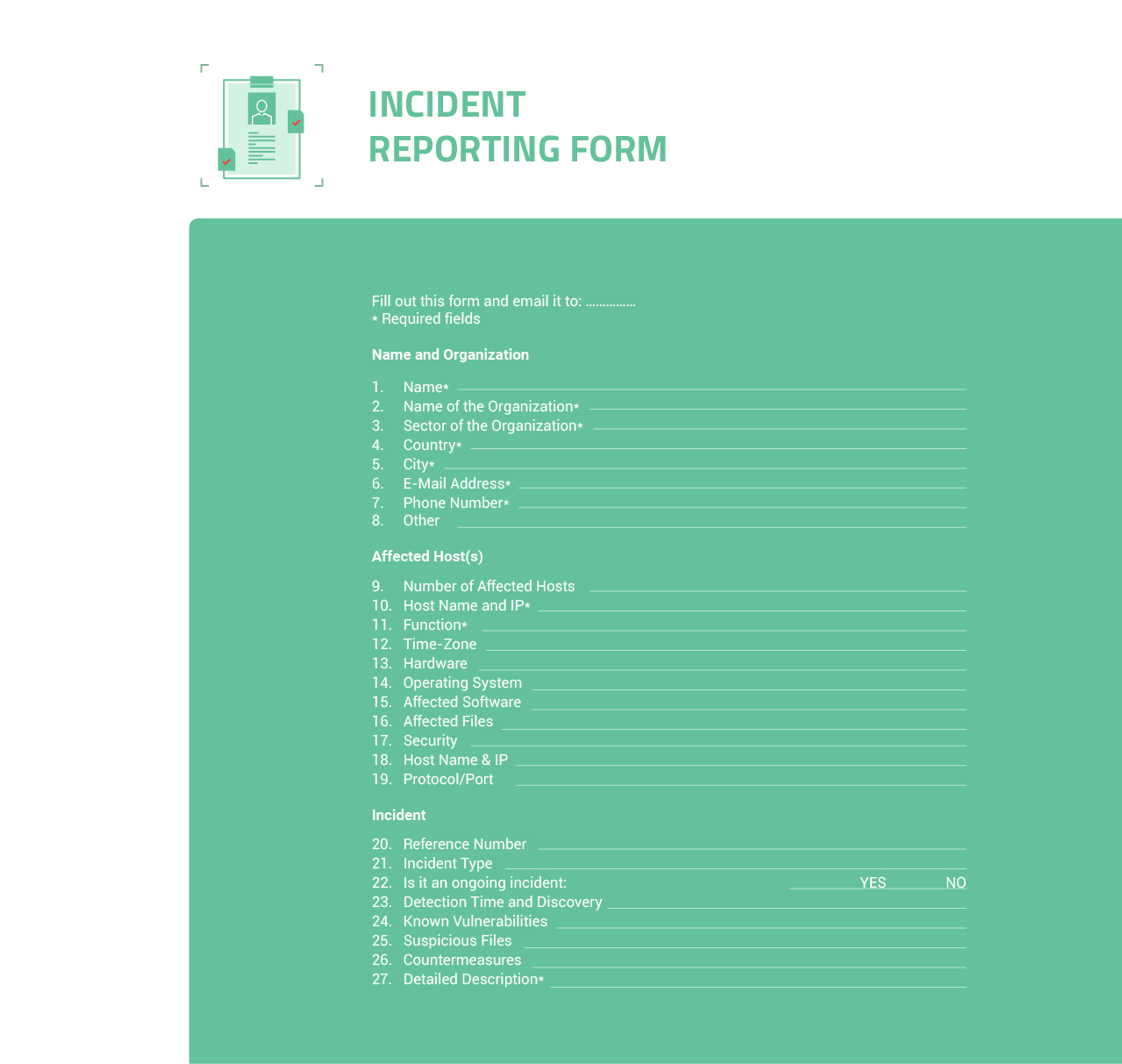
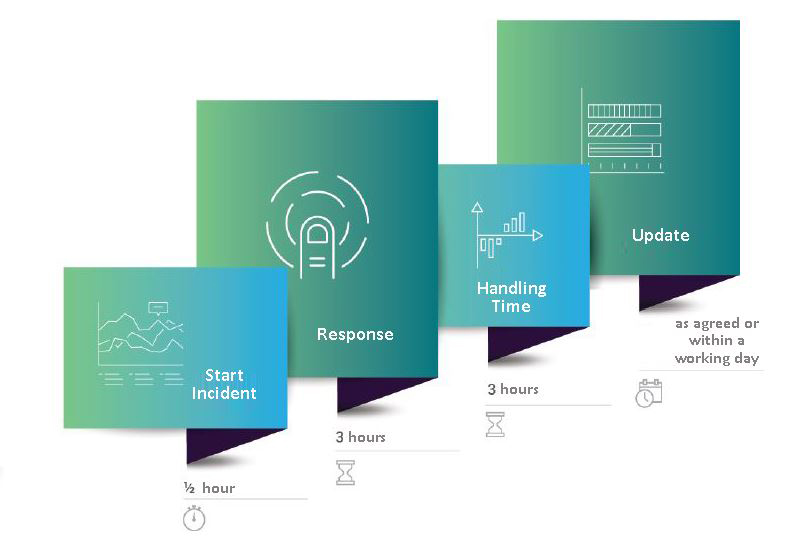
- Incident Handling: analysis of incidents by collecting forensic evidence, taking actions for the protection of affected systems, establishing mitigation strategies regarding incidents, recovering systems, tracking or tracing the compromised systems, conducting incident response on site, providing incident response support, enabling incident response coordination among the affected parties.
- Vulnerability Handling: obtaining information about hardware and software vulnerabilities, conducting vulnerability analysis through technical analysis and examination, responding vulnerabilities by developing or searching patches or fixes, developing strategies for detecting and removing vulnerabilities, enabling coordination for responding the detected vulnerabilities.
- Artifact Handling: conducting artifact analysis through identification and classification, removing or preventing artifacts by using signatures, enabling artifact response coordination.
2) Proactive Services focus on detecting and preventing attacks before an incident occurs. The main aim of these services is to avoid incidents and to reduce their impacts when they do occur. Thus, the information generated by the UITSEC CERT is disseminated to its constituents for protecting their assets and avoiding being target of an attack. Some of the services in this category are listed below:
- Announcements: creating alerts for attacks, intrusions and vulnerabilities, informing constituents about the emerging or available threats and their impacts.
- Technology Watch: following developments in the field of cyber security, observing newly emerging threats and technologies, following cyber security news in addition to laws and regulations on security issues.
- Security Audits or Assessments: conducting best practice and infrastructure reviews, scanning networks and systems, performing penetration tests.
- Configuration and Maintenance: enabling configuration and maintenance of security tools, applications, infrastructures and services such as intrusion detection system, firewalls and virtual private networks.
- Development of Security Tools: developing tools to rebuild compromised hosts or increase the functionality of the existing security tools.
- Intrusion Detection Services: analyzing intrusion detection system logs, initiating respond process for detected incidents, informing the relevant parties about any detected intrusions, monitoring all security-related logs.
- Security-Related Information Dissemination: Disseminating useful information with an aim to improve security posture, documenting best practices, archiving security-related policies and procedures, distributing patch information.
3) Security Quality Management Services are requested by the constituents for review and improvement of the security posture of their organizations. These services are designed to improve the overall security of an organization. By leveraging the experiences gained in providing the reactive and proactive services described above, UITSEC CERT brings unique perspectives to these quality management services. These services incorporate feedbacks and lessons learned based on knowledge gained by responding to incidents, vulnerabilities and attacks. Some of the services in this category are listed below:
- Risk Analysis: conducting risk analysis by focusing on real or potential threats, assessing protection and improvement strategies regarding risks, analyzing risks that can affect the assets of the constituents.

- Business Continuity and Disaster Recovery Planning: establishing effective policies and procedures for responding incidents, ensuring the continuity of critical process within the organization in case of an emergency, creating plans for recovering disasters.
- Security Consulting: offering guidance for protecting the critical assets of the constituents, identifying requirements regarding new systems, devices or applications, supporting the constituents for producing security-related policies.
- Awareness Building: increasing security-related awareness, supporting the constituents for the improvement of their security posture with appropriate security trainings, preparing newsletter, security bulletins or articles for increasing awareness of the constituents and its employees.
- Education & Training: organizing seminars, workshops or webinars with aim to inform constituents about important security issues, creating awareness through these trainings and supporting the improvement of the overall security of the constituents.
- Product Evaluation or Certification: conducting product evaluations regarding systems or applications, enabling the security of products, organizing certification programs for evaluating the products of the constituents.
UITSEC CERT’s daily work relies on tools and platforms which are developed with its own resources. According to your needs, UITSEC CERT can also offer additional services for you.


